For many people, online gaming is a serious business. Some players will go to any length to gain an advantage in their games, including launching distributed denial-of-service (DDoS) attacks that temporarily disable their opponents’ computers across the internet.
The best VPN services have a solution to protect you from such an attack. Using a gaming VPN, you can altogether avoid the effects of DDoS attacks.
What is DDoS in gaming?
In gaming, denial of service (DoS) and Distributed Denial of Service (DDoS) attacks that can knock thousands of players offline or cause lag spikes that put them at a disadvantage to rivals are common.

You may experience lag, delays, or dropouts if you cannot connect to the game servers consistently. Lag gives the opposing team the upper hand. A coordinated DDoS attack will often prevent you from accessing the game servers, effectively removing you from the competition.
How does a DDoS attack work?
DDoS attacks work by pouring internet traffic into your network or the infrastructure that surrounds it. Despite single-source denial-of-service attacks, traffic from a single source on the internet will not have a significant impact on network performance. Because DDoS attacks send traffic floods from multiple locations at once, they are more dangerous.
DDoS attacks are frequently launched from computers and devices that have been infected with malware. The malicious actor only needs to send a single command to the “botnet’s” thousands of “bots,” instructing them to target massive amounts of internet traffic at your IP address. Your network becomes overburdened, preventing you from adequately playing your game.
Is it possible to avoid DDoS attacks?
DDoS attacks have far-reaching consequences that are not limited to gamers. DDoS attacks have been launched against businesses, governments, and military operations, prompting the development of several mitigation strategies.
The majority of these methods necessitate the installation of an additional firewall between your network and the internet, which attempts to intelligently determine which traffic is legitimate and which should be routed to a virtual black hole.
Others limit the number of connections that each remote computer can make, effectively slowing down service for everyone while ensuring that legitimate visitors can still access the network in the event of a DDoS attack.
Another option is to spread incoming traffic across a distributed server network to avoid overloading a single server. Cloudflare, a cloud-based DDoS protection service that acts as a buffer between your network and the internet, is widely used by businesses.
These strategies may work for large corporations and governments, but they are out of reach for most gamers. Consider using a VPN to protect yourself from DDoS attacks while gaming.
The three types of DDoS attacks and how to protect from them?
The most severe problem with DDoS is its distributed nature. Attack sources can come from all over the world. It is not possible to block a specific packet source using dummy methods such as country.
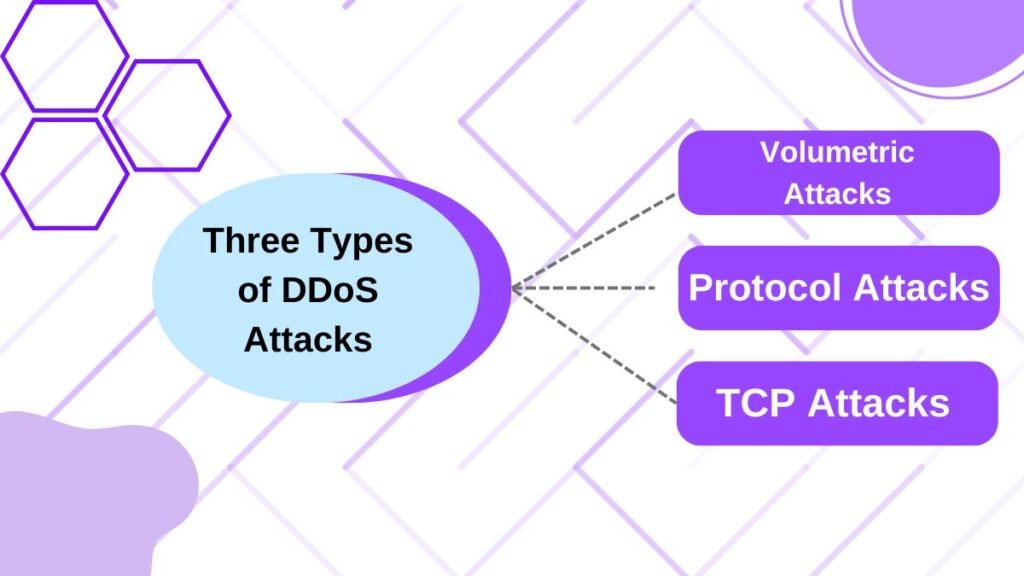
To understand how to protect against DDoS attacks, we must first comprehend the various types of DDoS attacks, as each type of attack necessitates a different type of defense. Volumetric, TCP, and application DDoS attacks are the three types of DDoS attacks.
Volumetric Attacks
Volumetric attacks rely on sending a large amount of data to the target. Amplifiers (misconfigured servers worldwide) can be used to amplify the attack and increase the bandwidth of the attacks. Even if we have some protection on-premises, these attacks are difficult to handle.
Although we can disconnect the connections, the data line has a limited capacity. There is still a lot of traffic on the data line if we drop the packets. As a result, locally installed security is insufficient.
The most crucial factor is to establish a reliable and automatic connection/signaling between the ISP and the on-premises DDoS protection appliance.
Application Attacks
The application layer is the focus of the last type. These attacks are the most damaging, but fortunately, they necessitate more information from the attackers. If the target application’s code contains flaws, these attacks can be carried out with only a few packets.
To mitigate these types of attacks, we can use a smart WAF or another application solution. However, because these attacks are targeted, it is necessary to investigate the attacks and repair or configure WAF for a specific application.
TCP Attacks
TCP attacks are designed to consume all of the target machine’s memory and other resources by exploiting vacant and available connection slots. Proxy servers that limit the number of requests and forward only the correct ones via a complete 3-way handshake can prevent these attacks.
Another method is to use source IP address reputation databases. Connections from shady origins, botnets, and “problematic” countries are either blocked or dropped. This is not a volumetric attack; our data line remains open even when we are under attack. The problem is solved by discarding unwanted packets.
Is it possible to protect against DDoS attacks with a VPN?
To understand how a VPN can help protect against DDoS attacks, consider that you connect to the internet using a unique IP address when you play an online game. Other players can easily see your IP address in many games. They then target this address with DDoS attacks.
When you use a VPN, your actual IP address is hidden. Instead, hackers will see the VPN server’s IP address. They can attack the VPN server’s IP address if they want to, but a secure VPN will have extensive DDoS protection, so the attacks will not slow down the network.
Why is defending against DDoS attacks so tricky?
During a DDoS attack, the mix of distributed attacking traffic and legitimate traffic is why they’re so difficult to defend. “Identifying your attacker against a background of legitimate users to your online service can be quite an art,” McKinnon says, “and when you only have one attacker (i.e. a traditional DoS attack), blocking them is quite simple.”
“However, when you’re being bombarded by hundreds or thousands of attackers at the same time, it takes time you don’t have—and you’re often fighting against limited bandwidth and access to stop the attack.”
Conclusion
We conclude the above article by saying that DDoS attacks are malicious attempts to bring down a network. They have coordinated attempts to knock you off gaming servers or cause lag by overloading your home network with internet traffic in the case of gaming.
A firewall can aid in the prevention of DDoS attacks. However, if you are constantly subjected to DDoS attacks, you should consider using a VPN service. When you use a VPN, your IP address is hidden from others, and any DDoS attacks are routed through the VPN provider. Many VPN services for gamers offer excellent DDoS protection, so you should be able to keep playing without interruption.


![Read more about the article What Is APM in Gaming? [2024 Updates]](https://wuschools.com/wp-content/uploads/2022/08/APM-in-Gaming-300x169.jpg)
